Solutions
Internet Access Control
As to Internet access control solutions, nowadays a single common approach prevails: either to inhibit the employees' access to all the sites, but for the specified ones or to permit access to all the resources, but for some of them.
Work Examiner product introduces a new approach to creation of Internet access control in your company. We offer not to inhibit or permit access of your employees to all websites in succession, but give consideration to what web-resources take most of the time of your personnel.
Obviously, the centralized solutions, such as a corporate firewall or proxy-server, are not capable to understand how much time Mike from the Sales department spends in myspace. And hits statistics from the site does not give such information and even misleads us! So, Mike, for instance, for half a day may be reading an article and discussions on his friend's site without opening new URL, i.e. without doing new hits.
To get true information about activity of a user one should apply client-server (but not server!) solution, including the solution installed on the employee's computer. This solution will continuously trace how much time is spent by the user on this or that site. Besides, it is desirable to register exactly the active time (involving user's actions, such as, for example, scrolling), but not just opened windows of browsers (a user may just go out to have lunch).
It is just this kind of innovation approach to internet access control that has been implemented in Work Examiner:

The figure shows that the Work Examiner allows absolute monitoring of not only corporate LAN PCs, but also remote employees, having alternative Internet access. In such a case the filters work without change (locally), and user activity data are loaded to the server as soon as the notebook obtain access to the server either via corporate LAN or from the Internet.
Internet access control rules are rather simple in setup, and at the same time they offer a number of interesting options.

For instance, besides usual application of rules to groups of users and web-sites, the Work Examiner can send a warning to your email each time the employee enters myspace.com.
You can create rules for users and computers with due account of hours of the day, days of the week, groups of web-sites, lists and groups of users or computers. Due to exclusion lists you can create permitting or inhibiting policies.
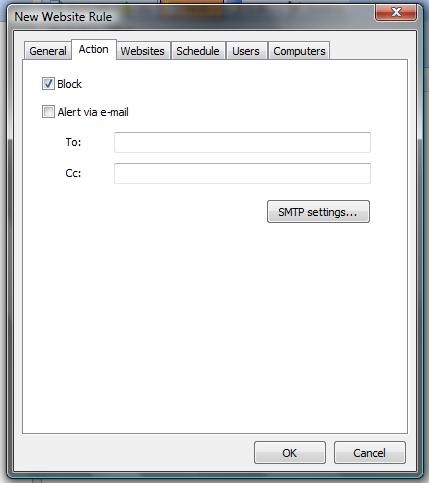
Internet access control rules also have a number of common features: users, computers, their groups, hours, days of the week, site groups.
Start to monitor employees instantly!
Install our solutions all over your network within 5 minutes